前言介紹
- 這款 WordPress 外掛「WP Content Security Plugin」是 2015-08-15 上架。
- 目前有 1000 個安裝啟用數。
- 上一次更新是 2018-02-10,距離現在已有 2639 天。超過一年沒更新,安裝要確認版本是否可用。以及後續維護問題!
- 外掛要求網站主機運作至少需要 PHP 版本 5.3 以上。
- 有 14 人給過評分。
- 還沒有人在論壇上發問,可能目前使用數不多,還沒有什麼大問題。
外掛協作開發者
dyland |
外掛標籤
csp | content security policy |
內容簡介
內容安全策略 (Content Security Policy, CSP) 是 W3C 的一項指導方針,旨在防止跨站腳本 (Cross-site scripting, XSS) 等攻擊。XSS 允許其他人在您的網站上運行腳本,使其不再是您的應用程式在您的網站上運行,並因「同源策略」而開啟您整個域名的攻擊風險 -- 您域名上任何地方的 XSS 都相當於您域名上的所有地方都會有 XSS 攻擊風險 (請參閱https://www.youtube.com/watch?v=WljJ5guzcLs)。
CSP 告訴瀏覽器對您的應用程式推送最低權限環境,只允許客戶端從可信任的域名使用資源,並阻止從其他任何地方使用所有資源。
添加 CSP 到您的網站將保護您的訪客免受以下攻擊:
跨站腳本 (XSS) 攻擊
在您的網站上的廣告軟件和間諜軟件
此外,此外掛還允許您忽略經常違反您策略的網站。例如,某些追踪圖像會顯示為違反您的策略,但您仍然不希望它們運行,因此您可以將該網站阻止出現在日誌中 -- 不過,請注意,瀏覽器仍然會呼叫您的服務器,並且您的服務器仍然會花費資源處理呼叫。
此外,此外掛可以幫助您進入 HSTS 預載列表 -- 詳情請參閱 https://hstspreload.org/。
CSP 指令
CSP 允許您控制您訪問者的瀏覽器可以從哪裡運行程式碼。
W3C 的指定允許以下指令:
default-src
default-src 是加載內容的默認策略。如果其他設置為空,則使用此設置。
script-src
定義 JavaScript 的有效來源。
style-src
定義樣式表的有效來源。
img-src
定義圖像的有效來源。
connect-src
適用於 XMLHttpRequest (AJAX)、WebSocket 或 EventSource。
manifest-src
指定可應用於資源的清單。
worker-src
指定 Worker、SharedWorker 或 ServiceWorker 腳本的有效來源。
font-src
定義字體的有效來源。
object-src
定義插件的有效來源。阻止您的網站成為驅動-by 滲透攻擊的來源。
media-src
定義聲音和影像的有效來源。
base-uri
限制可以在入口網站中使用的值的範圍。
frame-src
定義加載框架的有效來源。
sandbox
啟用類似於 iframe sandbox 屬性的請求資源的沙箱。
form-action
form-action 限制可以用作 HTML 表單元素操作的 URL。
frame-ancestors
是否允許嵌入使用框架、iframe、對象、嵌入等的資源在非 HTML 資源中。
plugin-types
通過限制可以嵌入的資源類型,限制可以調用的插件集。
report-uri
違反策略的資訊發佈到的 URL
原文外掛簡介
Content Security Policy (CSP) is a W3C guideline to prevent cross-site scripting (XSS) and related attacks. XSS allows other people to run scripts on your site, making it no
longer your application running on your site, and opens your whole domain to attack due to “Same-Origin Policy” – XSS anywhere on your domain is XSS everywhere on your domain. (see https://www.youtube.com/watch?v=WljJ5guzcLs)
CSP tells your browser to push least-privilege environment on your application, allowing the client to only use resources from trusted domains and block all resources from anywhere else.
Adding CSP to your site will protect your visitors from:
Cross-site scripting (XSS) attacks
Adware and Spyware while on your site
This plugin will help you set your CSP settings and will add them to the page the visitor requested. Policy violations will be logged in a database table which can be viewed via an admin page that supplies all the violations, along with counts. Buttons easily allow you to add the sites to your headers or to ignore them.
This plugin also allows you to ignore sites that repeatedly violate your policies. For example, some tracking images will show as violating your policies, but you still don’t want them to run, therefore you can block the site from showing up in your logs – note, however, that the browser will still call your server and your server will still spend resources processing the call.
In addition, this plugin can help you to get on the HSTS Preload list – See https://hstspreload.org/ for details.
CSP Directives
CSP allows you to control where your visitors’ browser can run code from.
The W3C specification allows for the following directives:
default-src
The default-src is the default policy for loading content. If another setting is blank then this setting will be used.
script-src
Defines valid sources of JavaScript.
style-src
Defines valid sources of stylesheets.
img-src
Defines valid sources of images.
connect-src
Applies to XMLHttpRequest (AJAX), WebSocket or EventSource.
manifest-src
Specifies which manifest can be applied to the resource
worker-src
Specifies valid sources for Worker, SharedWorker, or ServiceWorker scripts.
font-src
Defines valid sources of fonts.
object-src
Defines valid sources of plugins. Stops your site becoming the source of drive-by attacks.
media-src
Defines valid sources of audio and video.
base-uri
Limit the values that can be used in the entry.
frame-src
Defines valid sources for loading frames.
sandbox
Enables a sandbox for the requested resource similar to the iframe sandbox attribute.
form-action
The form-action restricts which URLs can be used as the action of HTML form elements.
frame-ancestors
Whether to allow embedding the resource using a frame, iframe, object, embed, etc. in non-HTML resources.
plugin-types
Restricts the set of plugins that can be invoked by limiting the types of resources that can be embedded.
report-uri
URL to post information on violations of the policies you set.
require-sri-for
Require integrity check for scripts and/or styles.
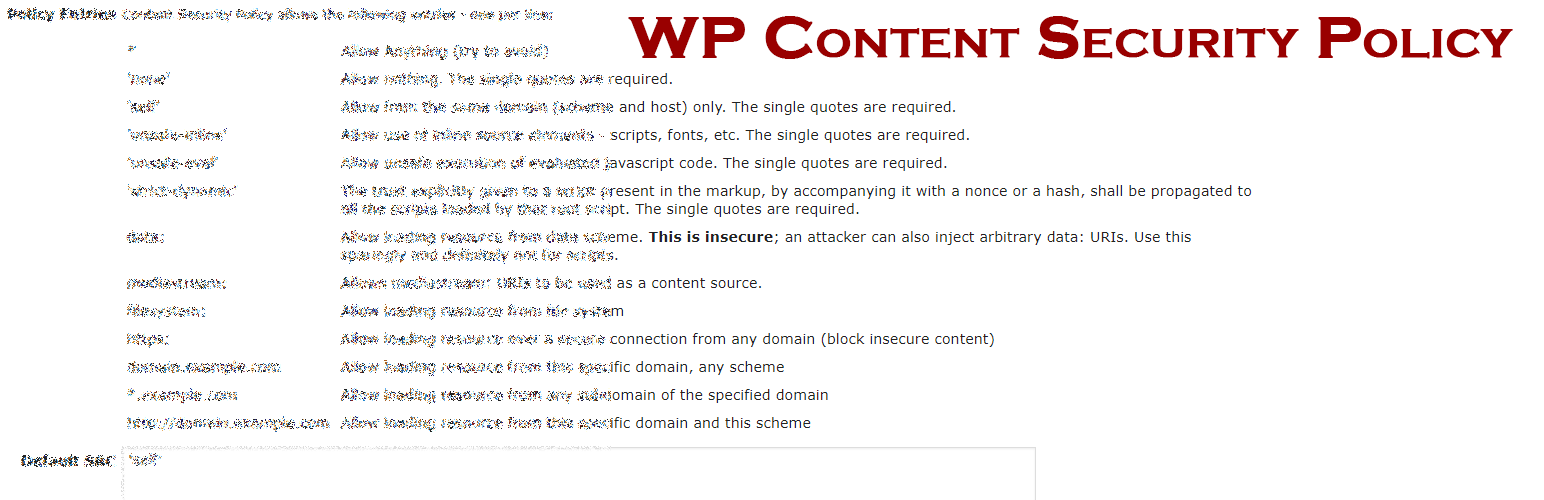
CSP Entry Syntax
Note – with version 3 of the CSP specification there has been a move to ‘strict-dynamic’ – see the Upgrade Notice section for more information.
Each directive can take one or more of the following values:
*
Allows loading resources from any source.
‘none’
Blocks loading resources from all sources. The single quotes are required.
‘self’
Refers to your own host. The single quotes are required.
‘unsafe-inline’
Allows inline elements, such as functions in script tags, onclicks, etc. The single quotes are required.
‘unsafe-eval’
Allows unsafe dynamic code evaluation such as JavaScript eval(). The single quotes are required.
‘strict-dynamic’
The trust explicitly given to a script present in the markup, by accompanying it with a nonce or a hash, shall be propagated to all the scripts loaded by that root script. The single quotes are required.
‘sha-AAAAAAAAA’
For scripts and styles that can’t take a nonce the browser will tell you a ‘sha-‘ value you can use. The single quotes are required.
‘nonce-AAAAAAAAA’
The trust nonce value – this value is automatically generated per page refresh and should not be entered by the user. The single quotes are required.
data:
Allow loading resources from data scheme – usually inline images. This is insecure; an attacker can also inject arbitrary data: URIs. Use this sparingly and definitely not for scripts.
mediastream:
Allows mediastream: URIs to be used as a content source.
filesystem:
Allow loading resource from file system.
https:
Only allows loading resources from HTTPS: on any domain. This can be used to block insecure requests.
www.example.com
Allow loading resources from this domain, using any scheme (http/https)
*.example.com
Allow loading resourcs from any subdomain under example.com, using any scheme (http/https)
http://www.example.com
Allows loading resources from this domain using this scheme.
/path/to/file/
Allows loading any file from this path on this domain.
/path/to/file/thefile
Allows loading this one file on this domain.
Security Headers
In addition to the CSP headers, there are other security headers supported, including:
Expect-CT
Instructs user agents (browsers) to expect valid Signed Certificate Timestamps (SCTs) to be served.
Strict Transport Security
The HTTP Strict-Transport-Security response header (HSTS) lets a web site tell browsers that it should only be accessed using HTTPS, instead of using HTTP.
X-Frame-Options
The X-Frame-Options HTTP response header can be used to indicate whether or not a browser should be allowed to render a page in a ,
X-XSS-Protection
The HTTP X-XSS-Protection response header is a feature of Internet Explorer, Chrome and Safari that stops pages from loading when they detect reflected cross-site scripting (XSS) attacks. Although these protections are largely unnecessary in modern browsers when sites implement a strong Content-Security-Policy that disables the use of inline JavaScript (‘unsafe-inline’), they can still provide protections for users of older web browsers that don’t yet support CSP.
X-Content-Type-Options
The X-Content-Type-Options response HTTP header is a marker used by the server to indicate that the MIME types advertised in the Content-Type headers should not be changed and be followed. This allows to opt-out of MIME type sniffing, or, in other words, it is a way to say that the webmasters knew what they were doing.
Referrer-Policy
The Referrer-Policy HTTP header governs which referrer information, sent in the Referer header, should be included with requests made.
Written By
This plugin was written by Dylan Downhill, CDO of Elixir Interactive .
各版本下載點
- 方法一:點下方版本號的連結下載 ZIP 檔案後,登入網站後台左側選單「外掛」的「安裝外掛」,然後選擇上方的「上傳外掛」,把下載回去的 ZIP 外掛打包檔案上傳上去安裝與啟用。
- 方法二:透過「安裝外掛」的畫面右方搜尋功能,搜尋外掛名稱「WP Content Security Plugin」來進行安裝。
(建議使用方法二,確保安裝的版本符合當前運作的 WordPress 環境。
1.2 | 1.3 | 1.4 | 1.5 | 1.6 | 1.7 | 1.8 | 1.9 | 2.0 | 2.1 | 2.2 | 2.3 | trunk |
延伸相關外掛(你可能也想知道)
Headers Security Advanced & HSTS WP 》Headers Security Advanced & HSTS WP 是一款超強大的全方位 WordPress 免費外掛。如果停用這個外掛,你的網站設定會恢復到停用之前的狀態。, , Headers ...。
GD Security Headers 》此外掛程式可設定多項與安全相關的 HTTP 標頭,包括內容安全策略、功能策略、轉送者策略等,其中 CSP 和 XSS 控制外掛支援報告記錄功能,使用兩個額外的資料...。
Content Security Policy Manager 》Content Security Policy Manager 是一個 WordPress 外掛,允許您輕鬆配置網站內容安全政策標頭。您可以為管理介面、已登入使用者的前端和常規訪客的前端設定...。
 No unsafe-inline 》內容安全策略(Content Security Policy, CSP)是一種計算機安全標準,旨在防止跨站腳本(XSS)、點擊劫持及其他代碼注入攻擊,在信任的網頁上下文中執行惡意內容...。
No unsafe-inline 》內容安全策略(Content Security Policy, CSP)是一種計算機安全標準,旨在防止跨站腳本(XSS)、點擊劫持及其他代碼注入攻擊,在信任的網頁上下文中執行惡意內容...。 CSP-ANTS&ST 》為了讓你的網站完全安全,你必須避免在你的內容安全政策標頭中使用 ‘unsafe-eval’ 和 ‘unsafe-inline’。, 這個外掛會在 script/styl...。
CSP-ANTS&ST 》為了讓你的網站完全安全,你必須避免在你的內容安全政策標頭中使用 ‘unsafe-eval’ 和 ‘unsafe-inline’。, 這個外掛會在 script/styl...。 Sentinel Headers Unlimited Extension 》中文翻譯, Sentinel Headers Unlimited Extension 是一個最佳的免費插件,適用於所有 WordPress 使用者。如果停用此插件,您的網站配置將恢復到之前的狀態。,...。
Sentinel Headers Unlimited Extension 》中文翻譯, Sentinel Headers Unlimited Extension 是一個最佳的免費插件,適用於所有 WordPress 使用者。如果停用此插件,您的網站配置將恢復到之前的狀態。,...。 SeaSP Community Edition 》SeaSP社群版是一個自動化的內容安全性政策管理器。SeaSP允許您為您的網站創建、配置、管理和部署內容安全政策。, WordPress SeaSP社群版外掛會記錄出現在您網...。
SeaSP Community Edition 》SeaSP社群版是一個自動化的內容安全性政策管理器。SeaSP允許您為您的網站創建、配置、管理和部署內容安全政策。, WordPress SeaSP社群版外掛會記錄出現在您網...。 Headit 》這個外掛提供了在網站回應中添加 HTTP headers 的簡單方式。, 這些 headers 可以包括您的應用程式特定的自訂 headers,或者是安全相關的 headers。您可能希望...。
Headit 》這個外掛提供了在網站回應中添加 HTTP headers 的簡單方式。, 這些 headers 可以包括您的應用程式特定的自訂 headers,或者是安全相關的 headers。您可能希望...。GDPR Helper using CSP 》透過阻擋所有第三方請求,輕鬆遵守歐盟 GDPR。, 此插件的目標是盡可能簡單地阻擋所有不需要的請求,透過設置一般內容安全性政策實現。, 此外,此插件也支援某...。
WordSentinel 》總結: WordSentinel WordPress 外掛強化您的網站安全性,可設定 HTTP 安全標頭,並提供兩個知名服務的安全評分:Mozilla Observatory 及 Qualys SSL Labs。, ...。
